K
Kathleen Martin
Guest
Encryption is one of the most effective tools to protect data on network-attached storage. Even if cybercriminals gain access to the drives or intercept communications to or from them, encryption makes the data unreadable to anyone who does not have the cryptographic key.
Use NAS encryption to prevent unauthorized individuals from gaining access to confidential data at rest or in motion. The data might include credit card numbers, intellectual property, medical records, personally identifiable information (PII) or other types of confidential data. Also, use encryption to comply with regulations such as GDPR or HIPAA.
Without encryption, data is stored and transmitted as clear text, which can be read by anyone who intercepts communications or gains access to the drives. A NAS device also shares the same LAN as other devices and traffic. These systems include computers, printers, smartphones, tablets and IoT devices.
NAS encryption can be a complex process and, if done incorrectly, can put sensitive data at risk. However, administrators can make their jobs easier by following these seven best practices.
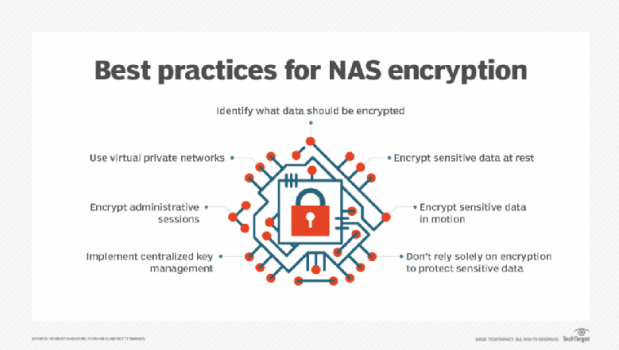
1. Identify what to encrypt
Encrypting and decrypting data can slow performance, sometimes significantly. The extent of the impact depends on the NAS device, how the organization implements encryption and whether the storage unit includes a cryptographic accelerator. In some cases, encryption can also make data reduction techniques less effective.
Encrypt only the data that needs protection or that applicable regulations govern. Prioritize the data based on its requirements for confidentiality. To help prioritize data, consider what the repercussions would be if certain types of data were compromised.
2. Encrypt sensitive data at rest
At-rest data refers to the data stored on the NAS device, as opposed to the data transmitted between endpoints. This doesn't preclude copies of the data from being transmitted, but the core data itself is persisted to the NAS media.
Use NAS encryption to protect sensitive data from unauthorized access, even if a device is stolen. However, ensure that the cryptographic modules used for the encryption and decryption operations have been validated against recognized standards such as the Federal Information Processing Standards developed by NIST.
Continue reading: https://searchstorage.techtarget.com/tip/7-NAS-encryption-best-practices-to-protect-data
Use NAS encryption to prevent unauthorized individuals from gaining access to confidential data at rest or in motion. The data might include credit card numbers, intellectual property, medical records, personally identifiable information (PII) or other types of confidential data. Also, use encryption to comply with regulations such as GDPR or HIPAA.
Without encryption, data is stored and transmitted as clear text, which can be read by anyone who intercepts communications or gains access to the drives. A NAS device also shares the same LAN as other devices and traffic. These systems include computers, printers, smartphones, tablets and IoT devices.
NAS encryption can be a complex process and, if done incorrectly, can put sensitive data at risk. However, administrators can make their jobs easier by following these seven best practices.
1. Identify what to encrypt
Encrypting and decrypting data can slow performance, sometimes significantly. The extent of the impact depends on the NAS device, how the organization implements encryption and whether the storage unit includes a cryptographic accelerator. In some cases, encryption can also make data reduction techniques less effective.
Encrypt only the data that needs protection or that applicable regulations govern. Prioritize the data based on its requirements for confidentiality. To help prioritize data, consider what the repercussions would be if certain types of data were compromised.
2. Encrypt sensitive data at rest
At-rest data refers to the data stored on the NAS device, as opposed to the data transmitted between endpoints. This doesn't preclude copies of the data from being transmitted, but the core data itself is persisted to the NAS media.
Use NAS encryption to protect sensitive data from unauthorized access, even if a device is stolen. However, ensure that the cryptographic modules used for the encryption and decryption operations have been validated against recognized standards such as the Federal Information Processing Standards developed by NIST.
Continue reading: https://searchstorage.techtarget.com/tip/7-NAS-encryption-best-practices-to-protect-data