K
Kathleen Martin
Guest
Full device takeover possible.
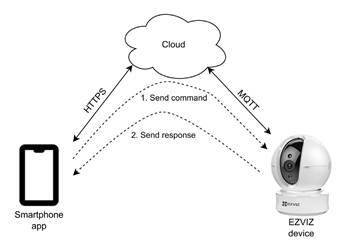
Researchers at security vendor Bitdefender have found a series of serious vulnerabilities which could be used to remotely control EZVIZ networked cameras without authentication, in order to download and decrypt images.
Bitdefender was able to create an attack chain of four different bugs to take over the EZVIZ cameras, exploiting a stack buffer overflow, and vulnerable application programming interface endpoints.
Together, the attack chain would lead to full camera takeover with video feed access.
Bitdefender was also able capture the encryption key for images and recover the administrator password.
The cameras are sold and used in Australia and New Zealand.
Camera firmware version 5.3.0 build 201719 was found to contain the vulnerabilities, but Bitdefender said earlier versions could also be vulnerable [pdf].
EZVIZ has issued patches for the affected cameras.
Continue reading: https://www.itnews.com.au/news/ezviz-video-cameras-can-be-accessed-remotely-585340
Researchers at security vendor Bitdefender have found a series of serious vulnerabilities which could be used to remotely control EZVIZ networked cameras without authentication, in order to download and decrypt images.
Bitdefender was able to create an attack chain of four different bugs to take over the EZVIZ cameras, exploiting a stack buffer overflow, and vulnerable application programming interface endpoints.
Together, the attack chain would lead to full camera takeover with video feed access.
Bitdefender was also able capture the encryption key for images and recover the administrator password.
The cameras are sold and used in Australia and New Zealand.
Camera firmware version 5.3.0 build 201719 was found to contain the vulnerabilities, but Bitdefender said earlier versions could also be vulnerable [pdf].
EZVIZ has issued patches for the affected cameras.
Continue reading: https://www.itnews.com.au/news/ezviz-video-cameras-can-be-accessed-remotely-585340